Understanding Bad USB Devices and Their Risks
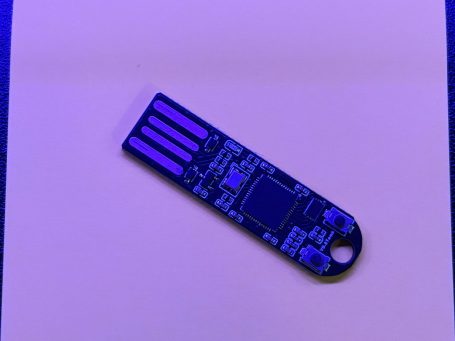
The most well-known device is the Rubber Ducky by HAK5, which is cleverly disguised as a flash drive, though it can also mimic other devices. It can seamlessly blend in and, when plugged into a computer, acts like a mouse, headset, or keyboard, capable of typing at astonishing speeds to deliver malicious payloads to the targeted system. These payloads can be used to capture credentials, exfiltrate data, perform reconnaissance, provide remote access, download malware, and launch various cyberattacks. To safeguard yourself, consider using a Malicious Cable Detector from O.MG. There are also specialized programs designed to monitor your typing speed in the background, but they may not be fast enough to counteract a threatening payload. Always remember that strong passwords are your best ally, and setting a password for running CMD as an administrator is wise. Other popular BAD USB devices include the Flipper Zero, and many hobbyists are creating their own versions using Raspberry Pi.
©Copyright. All rights reserved.
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.